本次实验在华为ensp模拟器具体实现。
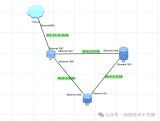
拓扑图
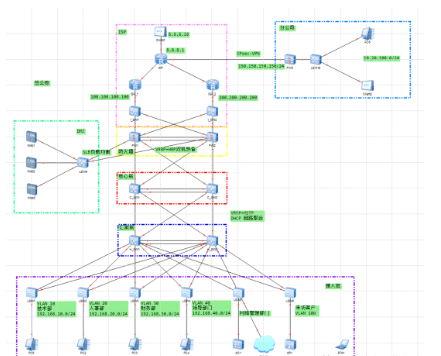
网段划分
| 区域 | VLAN | 网段 |
|---|---|---|
| 技术部 | VLAN 10 | 192.168.10.0/24 |
| 人事部 | VLAN 20 | 192.168.20.0/24 |
| 财务部 | VLAN 30 | 192.168.30.0/24 |
| 领导部门 | VLAN 40 | 192.168.40.0/24 |
| 来访客户 | VLAN 100 | 192.168.100.0/24 |
| 服务器DMZ | VLAN 90 | 192.138.90.0/24 |
办公区
VLAN+端口配置(二层)
LSW1
vlanbatch10
inte0/0/1
portlink-typetrunk
porttrunkallow-passvlan10
inte0/0/2
portlink-typetrunk
porttrunkallow-passvlan10
inte0/0/10
portlink-typeaccess
portdefaultvlan10
LSW2
vlanbatch20
inte0/0/1
portlink-typetrunk
porttrunkallow-passvlan20
inte0/0/2
portlink-typetrunk
porttrunkallow-passvlan20
inte0/0/10
portlink-typeaccess
portdefaultvlan20
LSW3
vlanbatch30
inte0/0/1
portlink-typetrunk
porttrunkallow-passvlan30
inte0/0/2
portlink-typetrunk
porttrunkallow-passvlan30
inte0/0/10
portlink-typeaccess
portdefaultvlan30
LSW4
vlanbatch40
inte0/0/1
portlink-typetrunk
porttrunkallow-passvlan40
inte0/0/2
portlink-typetrunk
porttrunkallow-passvlan40
inte0/0/10
portlink-typeaccess
portdefaultvlan40
H_SW1
vlanbatch10203040
intg0/0/1
portlink-typetrunk
porttrunkallow-passvlan10
intg0/0/2
portlink-typetrunk
porttrunkallow-passvlan20
intg0/0/3
portlink-typetrunk
porttrunkallow-passvlan30
intg0/0/4
portlink-typetrunk
porttrunkallow-passvlan40
H_SW2
vlanbatch10203040
intg0/0/1
portlink-typetrunk
porttrunkallow-passvlan10
intg0/0/2
portlink-typetrunk
porttrunkallow-passvlan20
intg0/0/3
portlink-typetrunk
porttrunkallow-passvlan30
intg0/0/4
portlink-typetrunk
porttrunkallow-passvlan40
无线网络配置
H_SW1
vlanbatch1001000
intg0/0/5
portlink-typetrunk
porttrunkallow-passvlanall
intg0/0/6
portlink-typetrunk
porttrunkallow-passvlan1001000
dhcpenable
intvlanif100
ipadd192.168.100.124
dhcpselectinterface
dhcpserverdns-list8.8.8.8
H_SW2
vlanbatch1001000
intg0/0/5
portlink-typetrunk
porttrunkallow-passvlanall
intg0/0/6
portlink-typetrunk
porttrunkallow-passvlan1001000
dhcpenable
LSW5
vlanbatch1001000
inte0/0/1
portlink-typetrunk
porttrunkallow-passvlanall
inte0/0/2
portlink-typetrunk
porttrunkallow-passvlanall
inte0/0/10
portlink-typetrunk
porttrunkallow-passvlan1001000
dhcpenable
LSW6
vlanbatch1001000
inte0/0/1
portlink-typetrunk
porttrunkallow-passvlan1001000
inte0/0/2
portlink-typetrunk
porttrunkallow-passvlan1001000
inte0/0/10
portlink-typetrunk
porttrunkallow-passvlan1001000
porttrunkpvidvlan1000
dhcpenable
AC
utm
sys
sysnameAC
vlanbatch1001000
intg0/0/1
portlink-typetrunk
porttrunkallow-passvlan1001000
dhcpenable
intvlanif1000
ipadd192.168.101.124
dhcpselectinterface
capwapsourceinterfaceVlanif1000
wlan
ap-groupnameap-group1
regulatory-domain-profiledefault
y
quit
apauth-modemac-auth
ap-id0ap-mac00e0-fc25-3910
ap-namearea_1
ap-groupap-group1
y
quit
security-profilenameWLAN
securitywpa-wpa2pskpass-phrasea1234567aes
quit
ssid-profilenameWLAN
ssidWLAN
quit
vap-profilenameWLAN
forward-modedirect-forward
service-vlanvlan-id100
security-profileWLAN
ssid-profileWLAN
quit
ap-groupnameap-group1
vap-profileWLANwlan1radio0
vap-profileWLANwlan1radio1
DHCP配置
H_SW1
dhcpenable
ippoolvlan10
gateway-list192.168.10.254
network192.168.10.0mask24
excluded-ip-address192.168.10.1192.168.10.10
excluded-ip-address192.168.10.150192.168.10.253
dns-list8.8.8.8
domain-nameblue.com
ippoolvlan20
gateway-list192.168.20.254
network192.168.20.0mask255.255.255.0
excluded-ip-address192.168.20.1192.168.20.10
excluded-ip-address192.168.20.150192.168.20.253
dns-list8.8.8.8
domain-nameblue.com
ippoolvlan30
gateway-list192.168.30.254
network192.168.30.0mask255.255.255.0
excluded-ip-address192.168.30.1192.168.30.10
excluded-ip-address192.168.30.150192.168.30.253
dns-list8.8.8.8
domain-nameblue.com
ippoolvlan40
gateway-list192.168.40.254
network192.168.40.0mask255.255.255.0
excluded-ip-address192.168.40.1192.168.40.10
excluded-ip-address192.168.40.150192.168.40.253
dns-list8.8.8.8
domain-nameblue.com
intvlanif10
ipadd192.168.10.1255.255.255.0
dhcpselectglobal
intvlanif20
ipadd192.168.20.1255.255.255.0
dhcpselectglobal
intvlanif30
ipadd192.168.30.1255.255.255.0
dhcpselectglobal
intvlanif40
ipadd192.168.40.1255.255.255.0
dhcpselectglobal
H_SW2
dhcpenable
ippoolvlan10
gateway-list192.168.10.254
network192.168.10.0mask255.255.255.0
excluded-ip-address192.168.10.1192.168.10.149
excluded-ip-address192.168.10.250192.168.10.253
dns-list8.8.8.8
domain-nameblue.com
ippoolvlan20
gateway-list192.168.20.254
network192.168.20.0mask255.255.255.0
excluded-ip-address192.168.20.1192.168.20.149
excluded-ip-address192.168.20.250192.168.20.253
dns-list8.8.8.8
domain-nameblue.com
ippoolvlan30
gateway-list192.168.30.254
network192.168.30.0mask255.255.255.0
excluded-ip-address192.168.30.1192.168.30.149
excluded-ip-address192.168.30.250192.168.30.253
dns-list8.8.8.8
domain-nameblue.com
ippoolvlan40
gateway-list192.168.40.254
network192.168.40.0mask255.255.255.0
excluded-ip-address192.168.40.1192.168.40.149
excluded-ip-address192.168.40.250192.168.40.253
dns-list8.8.8.8
domain-nameblue.com
interfaceVlanif10
ipaddress192.168.10.2255.255.255.0
dhcpselectglobal
interfaceVlanif20
ipaddress192.168.20.2255.255.255.0
dhcpselectglobal
interfaceVlanif30
ipaddress192.168.30.2255.255.255.0
dhcpselectglobal
interfaceVlanif40
ipaddress192.168.40.2255.255.255.0
dhcpselectglobal
在IP地址池创建的过程中,使用了excluded-ip-address命令,使得在主备交换机切换时分配的地址池相互排除,防止主备交换机切换后出现IP地址分配冲突导致网络故障。
VRRP配置
H_SW1
intvlanif10
vrrpvrid10virtual-ip192.168.10.254
vrrpvrid10priority105
intvlanif20
vrrpvrid20virtual-ip192.168.20.254
vrrpvrid20priority105
intvlanif30
vrrpvrid30virtual-ip192.168.30.254
intvlanif40
vrrpvrid40virtual-ip192.168.40.254
H_SW2
intvlanif10
vrrpvrid10virtual-ip192.168.10.254
intvlanif20
vrrpvrid20virtual-ip192.168.20.254
intvlanif30
vrrpvrid30virtual-ip192.168.30.254
vrrpvrid30priority105
intvlanif40
vrrpvrid40virtual-ip192.168.40.254
vrrpvrid40priority105
STP配置
LSW1
stpregion-configuration
region-nameBlue_mstp
revision-level1
instance10vlan10
activeregion-configuration
inte0/0/10
stpedged-portenable
LSW2
stpregion-configuration
region-nameBlue_mstp
revision-level1
instance10vlan10
activeregion-configuration
inte0/0/10
stpedged-portenable
LSW3
stpregion-configuration
region-nameBlue_mstp
revision-level1
instance30vlan30
activeregion-configuration
quit
inte0/0/10
stpedged-portenable
LSW4
stpregion-configuration
region-nameBlue_mstp
revision-level1
instance40vlan40
activeregion-configuration
inte0/0/10
stpedged-portenable
H_SW1
stpinstance12rootprimary
stpinstance34rootsecondary
stpregion-configuration
region-nameBlue_mstp
revision-level1
instance12vlan1020
instance34vlan3040
activeregion-configuration
intg0/0/11
stpdisable
intg0/0/12
stpdisable
H_SW2
stpinstance12rootsecondary
stpinstance34rootprimary
stpregion-configuration
region-nameBlue_mstp
revision-level1
instance12vlan1020
instance34vlan3040
activeregion-configuration
intg0/0/11
stpdisable
intg0/0/12
stpdisable
ACL配置
H_SW1
aclnumber3002
rule5denyipsource192.168.100.00.0.0.255destination192.168.0.00.0.255.255
intg0/0/5
traffic-filterinboundacl3002
H_SW2
aclnumber3002
rule5denyipsource192.168.100.00.0.0.255destination192.168.0.00.0.255.255
intg0/0/5
traffic-filterinboundacl3002
LACP配置
LACP链路聚合,链路聚合的原理是将一组相同属性的物理接口捆绑在一起为一个逻辑接口来增加带宽和可靠性的一种方法。有以下优势:
增加带宽、提高冗余(提高可靠性)、负载分担、节省成本、配置量小
1.增加带宽:链路聚合接口的最大带宽可以达到各个成员接口带宽之和。
2提高冗余:当某条路线出现故障的时候,流量可以切到其他可用的成员链路上。流量会切到其他可用链路上,从而提高链路聚合接口的冗余性。并不会影响数据的传输,相对来说也具有稳定性。
3负载分担:在一个链路聚合组内,可以实现在各成员活动链路上的负载分担。
4节省成本:管理员不需要升级链路速度,对已有的接口进行捆绑。
5配置量小:大部分的配置在组Eth-Trunk下完成。
主要的优势是能增加带宽、提高可靠性和负载分担。
H_SW1
lacppriority100
inteth-trunk1
portlink-typetrunk
porttrunkallow-passvlan10203040
modelacp-static
load-balancesrc-dst-mac
intg0/0/13
eth-trunk1
lacppriority100
intg0/0/14
eth-trunk1
H_SW2
inteth-trunk1
portlink-typetrunk
porttrunkallow-passvlan10203040
modelacp-static
load-balancesrc-dst-mac
intg0/0/13
eth-trunk1
intg0/0/14
eth-trunk1
OSPF配置
LSW1
intloopback0
ipadd192.168.1.132
LSW2
interfaceLoopBack0
ipaddress192.168.2.2255.255.255.255
LSW3
interfaceLoopBack0
ipaddress192.168.3.3255.255.255.255
LSW4
interfaceLoopBack0
ipaddress192.168.4.4255.255.255.255
H_SW1
intloopback0
ipadd192.168.5.532
ospf10router-id192.168.5.5
silent-interfaceVlanif10
silent-interfaceVlanif20
silent-interfaceVlanif30
silent-interfaceVlanif40
area0
network192.168.5.50.0.0.0
network192.168.10.10.0.0.0
network192.168.20.10.0.0.0
network192.168.30.10.0.0.0
network192.168.40.10.0.0.0
network192.168.25.50.0.0.0
network192.168.35.50.0.0.0
network192.168.100.10.0.0.0
H_SW2
interfaceLoopBack0
ipaddress192.168.6.6255.255.255.255
ospf10router-id192.168.6.6
silent-interfaceVlanif10
silent-interfaceVlanif20
silent-interfaceVlanif30
silent-interfaceVlanif40
area0.0.0.0
network192.168.6.60.0.0.0
network192.168.10.20.0.0.0
network192.168.20.20.0.0.0
network192.168.30.20.0.0.0
network192.168.40.20.0.0.0
network192.168.24.60.0.0.0
network192.168.36.60.0.0.0
network192.168.100.20.0.0.0
核心层
VLAN划分+配置端口
核心交换机
C_SW1
vlanbatch22to25
intg0/0/1
portlink-typeaccess
portdefaultvlan25
stpdisable
intg0/0/2
portlink-typeaccess
portdefaultvlan24
stpdisable
intg0/0/11
portlink-typeaccess
portdefaultvlan22
stpdisable
intg0/0/12
portlink-typeaccess
portdefaultvlan23
stpdisable
interfaceVlanif22
ipaddress192.168.22.7255.255.255.0
interfaceVlanif23
ipaddress192.168.23.7255.255.255.0
interfaceVlanif24
ipaddress192.168.24.7255.255.255.0
interfaceVlanif25
ipaddress192.168.25.7255.255.255.0
C_SW2
vlanbatch33to364455
intg0/0/1
portlink-typeaccess
portdefaultvlan35
stpdisable
intg0/0/2
portlink-typeaccess
portdefaultvlan36
stpdisable
intg0/0/11
portlink-typeaccess
portdefaultvlan34
stpdisable
intg0/0/12
portlink-typeaccess
portdefaultvlan33
stpdisable
interfaceVlanif33
ipaddress192.168.33.8255.255.255.0
interfaceVlanif34
ipaddress192.168.34.8255.255.255.0
interfaceVlanif35
ipaddress192.168.35.8255.255.255.0
interfaceVlanif36
ipaddress192.168.36.8255.255.255.0
interfaceVlanif44
ipaddress192.168.44.8255.255.255.0
interfaceVlanif55
ipaddress192.168.55.8255.255.255.0
汇聚层连接核心交换机
H_SW1
vlanbatch2535
intg0/0/11
portlink-typeaccess
portdefaultvlan25
stpdisable
intg0/0/12
portlink-typeaccess
portdefaultvlan35
stpdisable
intvlanif25
ipadd192.168.25.524
intvlanif35
ipadd192.168.35.524
H_SW2
vlanbatch2436
intg0/0/11
portlink-typeaccess
portdefaultvlan24
stpdisable
intg0/0/12
portlink-typeaccess
portdefaultvlan36
stpdisable
intvlanif24
ipadd192.168.24.624
intvlanif36
ipadd192.168.36.624
STP配置
C_SW1
intg0/0/1
stpdisable
intg0/0/2
stpdisable
intg0/0/11
stpdisable
intg0/0/12
stpdisable
C_SW2
intg0/0/1
stpdisable
intg0/0/2
stpdisable
intg0/0/11
stpdisable
intg0/0/12
stpdisable
LACP链路聚合
C_SW1
lacppriority100
inteth-trunk1
portlink-typetrunk
porttrunkallow-passvlan10203040
modelacp-static
load-balancesrc-dst-mac
intg0/0/3
eth-trunk1
lacppriority100
intg0/0/4
eth-trunk1
C_SW2
inteth-trunk1
portlink-typetrunk
porttrunkallow-passvlan10203040
modelacp-static
load-balancesrc-dst-mac
intg0/0/3
eth-trunk1
intg0/0/4
eth-trunk1
OSPF配置
C_SW1
interfaceLoopBack0
ipaddress192.168.7.7255.255.255.255
ospf10router-id192.168.7.7
area0.0.0.0
network192.168.7.70.0.0.0
network192.168.22.70.0.0.0
network192.168.23.70.0.0.0
network192.168.44.70.0.0.0
network192.168.55.70.0.0.0
network192.168.24.70.0.0.0
network192.168.25.70.0.0.0
C_SW2
interfaceLoopBack0
ipaddress192.168.8.8255.255.255.255
ospf10router-id192.168.8.8
area0.0.0.0
network192.168.8.80.0.0.0
network192.168.33.80.0.0.0
network192.168.34.80.0.0.0
network192.168.35.80.0.0.0
network192.168.36.80.0.0.0
network192.168.44.80.0.0.0
network192.168.55.80.0.0.0
防火墙
基本配置
FW1
用户名:admin
原始密码:Admin@123
密码:P@ssw0rd
新密码:Blue@123
undoterminalmonitor
language-modeChinese
sys
sysnameFW1
#配置连接防火墙web的接口,IP为虚拟网络对应网段的地址
intg0/0/0
undoipadd192.168.0.124
ipadd192.168.94.224
service-manageallpermit
FW2
用户名:admin
原始密码:Admin@123
密码:P@ssw0rd
新密码:Blue@123
undoterminalmonitor
language-modeChinese
sys
sysnameFW2
intg0/0/0
undoipadd192.168.0.124
ipadd192.168.94.324
service-manageallpermit
规划网段
FW1
intg1/0/0
undoshutdown
ipadd192.168.90.1255.255.255.0
intg1/0/1
undoshutdown
ipadd192.168.22.1255.255.255.0
service-manageallpermit
intg1/0/2
undoshutdown
ipadd192.168.34.1255.255.255.0
intg1/0/3
undoshutdown
intg1/0/4
undoshutdown
intg1/0/5
undoshutdown
ipaddress100.100.100.1255.255.255.0
service-managepingpermit
intg1/0/6
undoshutdown
ipadd200.200.200.1255.255.255.0
service-managepingpermit
FW2
intg1/0/0
undoshutdown
ipadd192.168.90.2255.255.255.0
intg1/0/1
undoshutdown
ipadd192.168.23.1255.255.255.0
service-manageallpermit
intg1/0/2
undoshutdown
ipadd192.168.33.1255.255.255.0
intg1/0/3
undoshutdown
intg1/0/4
undoshutdown
intg1/0/5
undoshutdown
ipaddress100.100.100.2255.255.255.0
service-managepingpermit
intg1/0/6
undoshutdown
ipadd200.200.200.2255.255.255.0
LACP链路聚合
FW1
inteth-trunk2
ipadd192.168.2.1255.255.255.0
modelacp-static
intg1/0/3
eth-trunk2
intg1/0/4
eth-trunk2
FW2
inteth-trunk2
ipadd192.168.2.2255.255.255.0
modelacp-static
intg1/0/3
eth-trunk2
intg1/0/4
eth-trunk2
规划安全区域
根据拓扑,将接口划入对应的安全区域
注意:两个防火墙之间的心跳接口要必须放进信任区域
FW1
firewallzonetrust
addintg1/0/1
addintg1/0/2
firewallzonedmz
addintg1/0/0
firewallzonenameheartid4
setpriority75
addinteth-trunk2
firewallzonenameISP1id5
setpriority20
addintg1/0/5
firewallzonenameISP2id6
setpriority15
addintg1/0/6
FW2
firewallzonetrust
addintg1/0/1
addintg1/0/2
firewallzonedmz
addintg1/0/0
firewallzonenameheartid4
setpriority75
addinteth-trunk2
firewallzonenameISP1id5
setpriority15
addintg1/0/5
firewallzonenameISP2id6
setpriority20
addintg1/0/6
指定链路接口组名称
FW1
ispname"chinamobile"linkif-group63
ispname"chinaunicom"linkif-group62
ispname"chinatelecom"linkif-group61
ispname"chinaeducationnet"linkif-group60
FW2
ispname"chinamobile"linkif-group63
ispname"chinaunicom"linkif-group62
ispname"chinatelecom"linkif-group61
ispname"chinaeducationnet"linkif-group60
安全策略精要
BGP、BFD、DHCP、DHCPv6、LDP和OSPF是否受安全策略控制,由基础协议控制开关(firewall packet-filter basic-protocol enable)决定。
FW1
firewallpacket-filterbasic-protocolenable
firewalldefendport-scanenable
firewalldefendip-sweepenable
firewalldefendteardropenable
firewalldefendtime-stampenable
firewalldefendroute-recordenable
firewalldefendsource-routeenable
firewalldefendip-fragmentenable
firewalldefendtcp-flagenable
firewalldefendwinnukeenable
firewalldefendfraggleenable
firewalldefendtracertenable
firewalldefendicmp-unreachableenable
firewalldefendicmp-redirectenable
firewalldefendlarge-icmpenable
firewalldefendping-of-deathenable
firewalldefendsmurfenable
firewalldefendlandenable
firewalldefendip-spoofingenable
FW2
firewallpacket-filterbasic-protocolenable
firewalldefendport-scanenable
firewalldefendip-sweepenable
firewalldefendteardropenable
firewalldefendtime-stampenable
firewalldefendroute-recordenable
firewalldefendsource-routeenable
firewalldefendip-fragmentenable
firewalldefendtcp-flagenable
firewalldefendwinnukeenable
firewalldefendfraggleenable
firewalldefendtracertenable
firewalldefendicmp-unreachableenable
firewalldefendicmp-redirectenable
firewalldefendlarge-icmpenable
firewalldefendping-of-deathenable
firewalldefendsmurfenable
firewalldefendlandenable
firewalldefendip-spoofingenable
安全策略配置
FW1
security-policy
#管理区
rulenameTrust_Local
descriptionManagement
source-zonetrust
destination-zonelocal
actionpermit
FW2
security-policy
#管理区
rulenameTrust_Local
descriptionManagement
source-zonetrust
destination-zonelocal
actionpermit
配置IP-link
FW1
ip-linkcheckenable
ip-linknameisp1
destination100.100.100.100interfaceGigabitEthernet1/0/5modeicmp
ip-linknameisp2
destination200.200.200.200interfaceGigabitEthernet1/0/6modeicmp
#安全策略配置
security-policy
rulenameLocal_ISP
descriptionip-link
source-zonelocal
destination-zoneISP1
destination-zoneISP2
actionpermit
FW2
ip-linkcheckenable
ip-linknameisp1
destination100.100.100.100interfaceGigabitEthernet1/0/5modeicmp
ip-linknameisp2
destination200.200.200.200interfaceGigabitEthernet1/0/6modeicmp
#安全策略配置
security-policy
rulenameLocal_ISP
descriptionip-link
source-zonelocal
destination-zoneISP1
destination-zoneISP2
actionpermit
配置静态路由
FW1
iproute-static0.0.0.00.0.0.0100.100.100.100preference50trackip-linkisp1
iproute-static0.0.0.00.0.0.0200.200.200.200preference50
iproute-static10.20.100.0255.255.255.0GigabitEthernet1/0/5100.100.100.100
iproute-static10.20.100.0255.255.255.0GigabitEthernet1/0/6200.200.200.200
iproute-static10.20.100.0255.255.255.0NULL0
FW2
iproute-static0.0.0.00.0.0.0100.100.100.100
iproute-static0.0.0.00.0.0.0200.200.200.200preference50
iproute-static10.20.100.0255.255.255.0GigabitEthernet1/0/5100.100.100.100
iproute-static10.20.100.0255.255.255.0GigabitEthernet1/0/6200.200.200.200
iproute-static10.20.100.0255.255.255.0NULL0
配置OSPF动态路由
步骤一:配置动态路由
FW1
interfaceLoopBack0
ipaddress192.168.11.11255.255.255.255
ospf10router-id192.168.11.11
default-route-advertise
area0.0.0.0
network192.168.11.110.0.0.0
network192.168.22.10.0.0.0
network192.168.34.10.0.0.0
network192.168.90.10.0.0.0
FW2
interfaceLoopBack0
ipaddress192.168.22.22255.255.255.255
ospf10router-id192.168.22.22
default-route-advertise
area0.0.0.0
network192.168.22.220.0.0.0
network192.168.23.10.0.0.0
network192.168.33.10.0.0.0
network192.168.90.20.0.0.0
步骤二:配置安全策略
FW1
security-policy
rulenameLocal_Trust
descriptionOSPF
source-zonelocal
destination-zonetrust
actionpermit
FW2
security-policy
rulenameLocal_Trust
descriptionOSPF
source-zonelocal
destination-zonetrust
actionpermit
双机热备
步骤1:配置VRRP备份组
主设备:FW1
intg1/0/5
vrrpvrid1virtual-ip100.100.100.5active
vrrpvirtual-macenable
intg1/0/6
vrrpvrid2virtual-ip200.200.200.5standby
vrrpvirtual-macenable
备份设备:FW2
intg1/0/5
vrrpvrid1virtual-ip100.100.100.5standby
vrrpvirtual-macenable
intg1/0/6
vrrpvrid2virtual-ip200.200.200.5active
vrrpvirtual-macenable
步骤2:开启HRP协议,并配置心跳接口和会话备份功能
FW1
hrpenable
hrpinteth-trunk2remote192.168.2.2
hrpmirrorsessionenable
hrpstandbyconfigenable
FW2
hrpenable
hrpinteth-trunk2remote192.168.2.1
hrpmirrorsessionenable
hrpstandbyconfigenable
步骤3:配置安全策列
是内网用户可以访问服务器和外网用户;外网用户只能访问服务器。
注意:只需要配置Master即可,Backup设备不用配置,配置命令会自动从主设备备份到备份设备。
FW1
security-policy
rulenameheart
source-zoneheart
source-zonelocal
destination-zoneheart
destination-zonelocal
actionpermit
FW2
security-policy
defaultactionpermit
rulenameheart
source-zoneheart
source-zonelocal
destination-zoneheart
destination-zonelocal
actionpermit
NAT配置
定义转换的IP地址范围
FW1
ipaddress-setWeb_IPtypeobject
address0100.100.100.5mask32
address1200.200.200.5mask32
ipaddress-setPCtypeobject
address0192.168.10.0mask24
address1192.168.20.0mask24
address2192.168.30.0mask24
address 3 192.168.40.0 mask 24 来源:网络技术干货圈
FW2
ipaddress-setWeb_IPtypeobject
address0100.100.100.5mask32
address1200.200.200.5mask32
ipaddress-setPCtypeobject
address0192.168.10.0mask24
address1192.168.20.0mask24
address2192.168.30.0mask24
address3192.168.40.0mask24
配置安全策略
FW1
security-policy
rulenameTrust_ISP
descriptionNAT
source-zonetrust
destination-zoneISP1
destination-zoneISP2
source-addressaddress-setPC
actionpermit
FW2
security-policy
rulenameTrust_ISP
descriptionNAT
source-zonetrust
destination-zoneISP1
destination-zoneISP2
source-addressaddress-setPC
actionpermit
配置NAT策略
FW1
nataddress-groupisp10
modepat
section0100.100.100.1100.100.100.2
nataddress-groupisp21
modepat
section0200.200.200.1200.200.200.2
nat-policy
rulenameNO_NAT_ISP1
source-zonetrust
destination-zoneISP1
source-address192.168.10.0mask255.255.255.0
source-address192.168.20.0mask255.255.255.0
source-address192.168.30.0mask255.255.255.0
source-address192.168.40.0mask255.255.255.0
destination-address10.20.0.0mask255.255.0.0
actionno-nat
rulenameNO_NAT_ISP2
source-zonetrust
destination-zoneISP2
source-address192.168.10.0mask255.255.255.0
source-address192.168.20.0mask255.255.255.0
source-address192.168.30.0mask255.255.255.0
source-address192.168.40.0mask255.255.255.0
destination-address10.20.0.0mask255.255.0.0
actionno-nat
rulenameNAT_ISP1
source-zonetrust
destination-zoneISP1
actionsource-nataddress-groupisp1
rulenameNAT_ISP2
source-zonetrust
destination-zoneISP2
actionsource-nataddress-groupisp2
FW2
nataddress-groupisp10
modepat
section0100.100.100.1100.100.100.2
nataddress-groupisp21
modepat
section0200.200.200.1200.200.200.2
nat-policy
rulenameNO_NAT_ISP1
source-zonetrust
destination-zoneISP1
source-address192.168.10.0mask255.255.255.0
source-address192.168.20.0mask255.255.255.0
source-address192.168.30.0mask255.255.255.0
source-address192.168.40.0mask255.255.255.0
destination-address10.20.0.0mask255.255.0.0
actionno-nat
rulenameNO_NAT_ISP2
source-zonetrust
destination-zoneISP2
source-address192.168.10.0mask255.255.255.0
source-address192.168.20.0mask255.255.255.0
source-address192.168.30.0mask255.255.255.0
source-address192.168.40.0mask255.255.255.0
destination-address10.20.0.0mask255.255.0.0
actionno-nat
rulenameNAT_ISP1
source-zonetrust
destination-zoneISP1
actionsource-nataddress-groupisp1
rulenameNAT_ISP2
source-zonetrust
destination-zoneISP2
actionsource-nataddress-groupisp2
SNMP配置
FW1
snmp-agentsession-ratetrapthreshold100
FW2
snmp-agentsession-ratetrapthreshold100
IPsec配置
步骤一:配置ACL
FW1
aclnumber3000
rule5permitipsource192.168.0.00.0.255.255destination10.20.100.00.0.0.255
aclnumber3001
rule5permitipsource192.168.0.00.0.255.255destination10.20.100.00.0.0.255
FW2
aclnumber3000
rule5permitipsource192.168.0.00.0.255.255destination10.20.100.00.0.0.255
aclnumber3001
rule5permitipsource192.168.0.00.0.255.255destination10.20.100.00.0.0.255
步骤二:配置IPsec proposal
这是IKE阶段二的策略,在阶段二的策略中安全协议采用ESP,加密算法使用aes-256,验证算法使用sha2-256
FW1
ipsecproposalprop23101638529
encapsulation-modeauto
espauthentication-algorithmsha2-256
espencryption-algorithmaes-256
ipsecproposalprop23101639469
encapsulation-modeauto
espauthentication-algorithmsha2-256
espencryption-algorithmaes-256
FW2
ipsecproposalprop23101638529
encapsulation-modeauto
espauthentication-algorithmsha2-256
espencryption-algorithmaes-256
ipsecproposalprop23101639469
encapsulation-modeauto
espauthentication-algorithmsha2-256
espencryption-algorithmaes-256
步骤三:配置IKE proposal
配置IKE Proposal,这是IKE阶段一的策略,在FW1/FW2上部署的相关策略均需与FW3相匹配。IKE阶段一的策略中,身份验证使用的是预共享的认证方式,验证算法使用的是sha2-256,加密算法使用aes-256
FW1
ikeproposal1
encryption-algorithmaes-256
dhgroup14
authentication-algorithmsha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
ikeproposal2
encryption-algorithmaes-256
dhgroup14
authentication-algorithmsha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
FW2
ikeproposal1
encryption-algorithmaes-256
dhgroup14
authentication-algorithmsha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
ikeproposal2
encryption-algorithmaes-256
dhgroup14
authentication-algorithmsha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
步骤四:配置IKE peer
定义预共享秘钥、关联IKE proposal并指定隧道对端节点IP
FW1
ikepeerike231016385293
exchange-modeauto
pre-shared-key123.abc
ike-proposal1
local-id-typefqdn
remote-id-typenone
local-idC1
dpdtypeperiodic
ikenegotiatecompatible
ikepeerike231016394699
exchange-modeauto
pre-shared-key123.abc
ike-proposal2
local-id-typefqdn
remote-id-typenone
local-idc2
dpdtypeperiodic
ikenegotiatecompatible
FW2
ikepeerike231016385293
exchange-modeauto
pre-shared-key123.abc
ike-proposal1
local-id-typefqdn
remote-id-typenone
local-idC1
dpdtypeperiodic
ikenegotiatecompatible
ikepeerike231016394699
exchange-modeauto
pre-shared-key123.abc
ike-proposal2
local-id-typefqdn
remote-id-typenone
local-idC2
dpdtypeperiodic
ikenegotiatecompatible
步骤五:配置IPsec Policy
创建ipsec policy,绑定ipsec proposal、Ike peer、ACL感兴趣流、配置本地站点地址。
FW1
ipsecpolicy-templatetpl2310163852931
securityacl3000
ike-peerike231016385293
proposalprop23101638529
tunnellocal100.100.100.5
aliasIPsec-1
sadurationtraffic-based10485760
sadurationtime-based3600
routeinjectdynamic
ipsecpolicy-templatetpl2310163946991
securityacl3001
ike-peerike231016394699
proposalprop23101639469
tunnellocal200.200.200.5
aliasIPsec-2
sadurationtraffic-based10485760
sadurationtime-based3600
routeinjectdynamic
ipsecpolicyipsec231016385210000isakmptemplatetpl231016385293
ipsecpolicyipsec231016394610000isakmptemplatetpl231016394699
FW2
ipsecpolicy-templatetpl2310163852931
securityacl3000
ike-peerike231016385293
proposalprop23101638529
tunnellocal100.100.100.5
aliasIPsec-1
sadurationtraffic-based10485760
sadurationtime-based3600
routeinjectdynamic
ipsecpolicy-templatetpl2310163946991
securityacl3001
ike-peerike231016394699
proposalprop23101639469
tunnellocal200.200.200.5
aliasIPsec-2
sadurationtraffic-based10485760
sadurationtime-based3600
routeinjectdynamic
ipsecpolicyipsec231016385210000isakmptemplatetpl231016385293
ipsecpolicyipsec231016394610000isakmptemplatetpl231016394699
步骤六:应用IPsec Policy到接口
FW1
intg1/0/5
ipsecpolicyipsec2310163852master
intg1/0/6
ipsecpolicyipsec2310163946slave
FW2
intg1/0/5
ipsecpolicyipsec2310163852slave
intg1/0/6
ipsecpolicyipsec2310163946master
步骤七:配置策略
FW1
#基于策略路由
policy-based-route
rulenameTrust_DMZ1
source-zonetrust
destination-addressaddress-setWeb_IP
actionpbrnext-hop192.168.90.3
rulenameISP12
source-zonetrust
source-address192.168.10.0mask255.255.255.0
source-address192.168.20.0mask255.255.255.0
actionpbregress-interfaceGigabitEthernet1/0/5next-hop100.100.100.100
rulenameISP23
source-zonetrust
source-address192.168.30.0mask255.255.255.0
source-address192.168.40.0mask255.255.255.0
actionpbregress-interfaceGigabitEthernet1/0/6next-hop200.200.200.200
#安全策略配置
security-policy
rulenameISP_Local
descriptionIPSec
source-zoneISP1
source-zoneISP2
destination-zonelocal
destination-address100.100.100.5mask255.255.255.255
destination-address200.200.200.5mask255.255.255.255
actionpermit
rulenameISP_Trust
descriptionVPN
source-zoneISP1
source-zoneISP2
destination-zonetrust
destination-address192.168.0.0mask255.255.0.0
actionpermit
FW2
#基于策略路由
policy-based-route
rulenameTrust_DMZ1
source-zonetrust
destination-addressaddress-setWeb_IP
actionpbrnext-hop192.168.90.3
rulenameISP12
source-zonetrust
source-address192.168.10.0mask255.255.255.0
source-address192.168.20.0mask255.255.255.0
actionpbregress-interfaceGigabitEthernet1/0/5next-hop100.100.100.100
rulenameISP23
source-zonetrust
source-address192.168.30.0mask255.255.255.0
source-address192.168.40.0mask255.255.255.0
actionpbregress-interfaceGigabitEthernet1/0/6next-hop200.200.200.200
#安全策略配置
security-policy
rulenameISP_Local
descriptionIPSec
source-zoneISP1
source-zoneISP2
destination-zonelocal
destination-address100.100.100.5mask255.255.255.255
destination-address200.200.200.5mask255.255.255.255
actionpermit
rulenameISP_Trust
descriptionVPN
source-zoneISP1
source-zoneISP2
destination-zonetrust
destination-address192.168.0.0mask255.255.0.0
actionpermit
L2TP配置
打开防火墙的web界面,依次选择 对象->用户->default,然后新建一个用于登录L2TP VPN的用户,再点击应用。
FW1
l2tpenable
aaa
service-schemewebServerScheme1649076535499
quit
domaindefault
service-schemewebServerScheme1649076535499
service-typel2tpike
internet-accessmodepassword
referenceusercurrent-domain
manager-userpassword-modifyenable
manager-useraudit-admin
passwordcipherBlue@123
service-typewebterminal
level15
l2tp-group1
tunnelpasswordcipherblue@123
tunnelnameLNS
allowl2tpvirtual-template1remoteL2TP-Clientdomaindefault
interfaceVirtual-Template0
pppauthentication-modechap
y
remoteaddress172.16.1.10
ipaddress172.16.1.1255.255.255.0
service-managepingpermit
路由配置
接口配置地址
ISP
intg0/0/1
ipadd10.10.100.324
intg0/0/2
ipadd10.10.200.324
intg0/0/3
ipadd150.150.150.124
inte0/0/0
ipadd8.8.8.124
inte0/0/1
ipadd192.168.94.5024
ISP_1
intg0/0/1
ipadd100.100.100.10024
intg0/0/2
ipadd10.10.100.124
ISP_2
intg0/0/1
ipadd200.200.200.20024
intg0/0/2
ipadd10.10.200.224
配置IS-IS
ISP
intloopback0
ipadd3.3.3.332
isis26
network-entity49.0010.0030.0300.3003.00
is-levellevel-2
cost-stylewide
log-peer-changetopology
intg0/0/1
isisenable26
intg0/0/2
isisenable26
intg0/0/3
isisenable26
inte0/0/0
isisenable26
inte0/0/1
isisenable26
intloopback0
isisenable26
ISP_1
intloopback0
ipadd1.1.1.132
isis26
is-levellevel-2
cost-stylewide
network-entity49.0010.0010.0100.1001.00
log-peer-changetopology
intg0/0/1
isisenable26
intg0/0/2
isisenable26
intloopback0
isisenable26
ISP_2
intloopback0
ipadd2.2.2.232
isis26
is-levellevel-2
cost-stylewide
network-entity49.0010.0020.0200.2002.00
log-peer-changetopology
intg0/0/1
isisenable26
intg0/0/2
isisenable26
intloopback0
isisenable26
子公司配置
防火墙
初始化配置
用户名:admin
原始密码:Admin@123
密码:Blue@123
undoterminalmonitor
language-modeChinese
sys
sysnameFW3
intg0/0/0
undoipadd192.168.0.124
ipadd192.168.94.424
service-manageallpermit
规划网段
intg1/0/0
undoshutdown
ipadd150.150.150.150255.255.255.0
service-managepingpermit
intg1/0/1
undoshutdown
ipadd10.20.100.254255.255.255.0
service-managepingpermit
#创建Tunnel接口并绑定接口
intTunnel1
ipaddunnumberedintg1/0/0
aliasTunnel1
service-managepingpermit
intTunnel2
ipaddunnumberedintg1/0/0
aliasTunnel2
service-managepingpermit
规划安全区域
firewallzonetrust
addinterfaceGigabitEthernet1/0/1
firewallzoneuntrust
addinterfaceGigabitEthernet1/0/0
addinterfaceTunnel1
addinterfaceTunnel2
指定链路接口组名称
ispname"chinamobile"linkif-group63
ispname"chinaunicom"linkif-group62
ispname"chinatelecom"linkif-group61
ispname"chinaeducationnet"linkif-group60
安全策略配置
#基础协议控制开关
firewallpacket-filterbasic-protocolenable
#安全策略
security-policy
rulenameTrust_Untrust
source-zonetrust
destination-zoneuntrust
actionpermit
配置IP-Link
ip-linkcheckenable
ip-linknamelink_100
destination100.100.100.5interfaceGigabitEthernet1/0/1modeicmp
ip-linknamelink_200
destination200.200.200.5interfaceGigabitEthernet1/0/1modeicmp
配置静态路由
iproute-static0.0.0.00.0.0.0150.150.150.1
iproute-static192.168.0.0255.255.0.0NULL0
iproute-static192.168.10.0255.255.255.0Tunnel1preference10trackip-linklink_100
iproute-static192.168.10.0255.255.255.0Tunnel2preference20
iproute-static192.168.20.0255.255.255.0Tunnel1preference10trackip-linklink_100
iproute-static192.168.20.0255.255.255.0Tunnel2preference20
iproute-static192.168.30.0255.255.255.0Tunnel2preference10trackip-linklink_200
iproute-static192.168.30.0255.255.255.0Tunnel1preference20
iproute-static192.168.40.0255.255.255.0Tunnel2preference10trackip-linklink_200
iproute-static192.168.40.0255.255.255.0Tunnel1preference20
NAT配置
#配置NAT策略
nat-policy
rulenameNO_NAT
source-zonetrust
destination-zoneuntrust
source-address10.20.100.0mask255.255.255.0
destination-address192.168.0.0mask255.255.0.0
actionno-nat
rulenameNAT
source-zonetrust
destination-zoneuntrust
actionsource-nateasy-ip
配置IPSec VPN
步骤一:配置ACL
aclnumber3000
rule5permitipsource10.20.100.00.0.0.255destination192.168.0.00.0.255.255
aclnumber3001
rule5permitipsource10.20.100.00.0.0.255destination192.168.0.00.0.255.255
步骤二:配置IPSec proposal
ipsecproposalprop23101712198
encapsulation-modeauto
espauthentication-algorithmsha2-256
espencryption-algorithmaes-256
ipsecproposalprop23101713129
encapsulation-modeauto
espauthentication-algorithmsha2-256
espencryption-algorithmaes-256
步骤三:配置IKE proposal
ikeproposal1
encryption-algorithmaes-256
dhgroup14
authentication-algorithmsha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
ikeproposal2
encryption-algorithmaes-256
dhgroup14
authentication-algorithmsha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
步骤四:配置IKE peer
ikepeerike231017121983
exchange-modeauto
pre-shared-key123.abc
ike-proposal1
local-id-typefqdn
remote-id-typenone
local-idBr1
dpdtypeperiodic
remote-address100.100.100.5
ikepeerike231017131292
exchange-modeauto
pre-shared-key123.abc
ike-proposal2
local-id-typefqdn
remote-id-typenone
local-idBr2
dpdtypeperiodic
remote-address200.200.200.5
步骤五:配置IPSec Policy
ipsecpolicyipsec23101712191isakmp
securityacl3000
ike-peerike231017121983
proposalprop23101712198
tunnellocalapplied-interface
aliasIPSec-1
satrigger-modeauto
sadurationtraffic-based10485760
sadurationtime-based3600
routeinjectdynamic
ipsecpolicyipsec23101713121isakmp
securityacl3001
ike-peerike231017131292
proposalprop23101713129
tunnellocalapplied-interface
aliasIPSec-2
satrigger-modeauto
sadurationtraffic-based10485760
sadurationtime-based3600
routeinjectdynamic
步骤六:应用IPSec Policy到接口
intTunnel1
tunnel-protocolipsec
ipsecpolicyipsec2310171219
intTunnel2
tunnel-protocolipsec
ipsecpolicyipsec2310171312
步骤七:配置策略
security-policy
rulenameLocal_Untrust
descriptionIPSECUPD500
source-zonelocal
destination-zoneuntrust
destination-address100.100.100.5mask255.255.255.255
destination-address200.200.200.5mask255.255.255.255
actionpermit
rulenameUntrust_Local
descriptionIPSec_esp
source-zoneuntrust
destination-zonelocal
source-address100.100.100.5mask255.255.255.255
source-address200.200.200.5mask255.255.255.255
actionpermit
rulenameUntrust_Trust
descriptionVPN
source-zoneuntrust
destination-zonetrust
source-address192.168.0.0mask255.255.0.0
destination-address10.20.100.0mask255.255.255.0
actionpermit
服务区域DMZ
VLAN+端口配置
LSW9
vlanbatch90
intvlanif90
ipaddress192.168.90.3255.255.255.0
intg0/0/11
portlink-typeaccess
portdefaultvlan90
intg0/0/12
portlink-typeaccess
portdefaultvlan90
intg0/0/13
portlink-typeaccess
portdefaultvlan90
intg0/0/1
portlink-typeaccess
portdefaultvlan90
intg0/0/2
portlink-typeaccess
portdefaultvlan90
ospf配置
LSW9
intloopback0
ipadd192.168.9.932
ospf10router-id192.168.9.9
default-route-advertise
area0.0.0.0
network192.168.9.90.0.0.0
network192.168.90.30.0.0.0
安全策略配置
FW1
#外网访问服务、防火墙到服务器、内网访问服务
security-policy
rulenameISP_DMZ
descriptionWWW
source-zoneISP1
source-zoneISP2
destination-zonedmz
destination-addressaddress-setWeb_IP
servicedns
serviceftp
servicehttp
serviceicmp
long-linkenable
long-linkaging-time10
actionpermit
rulenameLocal_DMZ
descriptionOSPF
source-zonelocal
destination-zonedmz
destination-address192.168.90.0mask255.255.255.0
serviceicmp
actionpermit
rulenameTrust_DMZ
source-zonetrust
destination-zonedmz
servicehttp
actionpermit
FW2
security-policy
rulenameISP_DMZ
descriptionWWW
source-zoneISP1
source-zoneISP2
destination-zonedmz
destination-addressaddress-setWeb_IP
servicedns
serviceftp
servicehttp
serviceicmp
long-linkenable
long-linkaging-time10
actionpermit
rulenameLocal_DMZ
descriptionOSPF
source-zonelocal
destination-zonedmz
destination-address192.168.90.0mask255.255.255.0
serviceicmp
actionpermit
rulenameTrust_DMZ
source-zonetrust
destination-zonedmz
servicehttp
actionpermit
服务器负载均衡SLB
FW1
slbenable
slb
group0server
metricroundrobin
health-checktypeicmp
rserver1rip192.168.90.10port80max-connection10descriptionserver1
rserver2rip192.168.90.20port80max-connection20descriptionserver2
rserver3rip192.168.90.30port80max-connection30descriptionserver3
actionoptimize
vserver0WEB
vip0100.100.100.5
vip1200.200.200.5
protocolhttp
vport80
groupserver
FW2
slbenable
slb
group0server
metricroundrobin
health-checktypeicmp
rserver1rip192.168.90.10port80max-connection10descriptionserver1
rserver2rip192.168.90.20port80max-connection20descriptionserver2
rserver3rip192.168.90.30port80max-connection30descriptionserver3
actionoptimize
vserver0WEB
vip0100.100.100.5
vip1200.200.200.5
protocolhttp
vport80
groupserver
审核编辑 :李倩
-
华为
+关注
关注
216文章
34429浏览量
251662 -
VLAN
+关注
关注
1文章
278浏览量
35651 -
模拟器
+关注
关注
2文章
875浏览量
43218
原文标题:【项目案例】如何使用华为ensp模拟器设计实现企业网络?
文章出处:【微信号:网络工程师笔记,微信公众号:网络工程师笔记】欢迎添加关注!文章转载请注明出处。
发布评论请先 登录
相关推荐
华为ensp模拟器,通过wireshark抓包分析,更容易理解网络原理(下)#华为模拟器#wi#硬声创作季
玩转云企业网(上):为什么需要云企业网
企业网络,什么是企业网络
华为新版模拟器eNSP Lite

什么是eNSP?华为网络仿真平台eNSP的使用方法




 如何使用华为ensp模拟器设计实现企业网络?
如何使用华为ensp模拟器设计实现企业网络?











评论