本次实验基于CISCO CSR1000V的虚拟路由器进行
实验拓扑
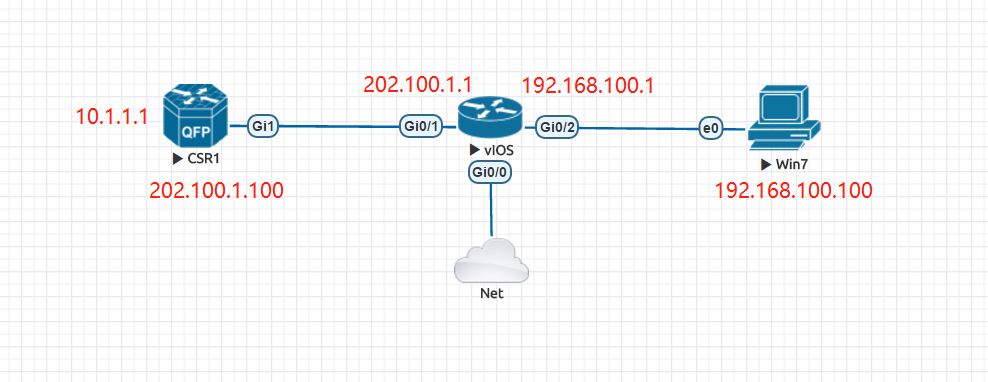 实验拓扑
实验拓扑
实验配置
hostnamecsr1kv ! aaanew-model ! aaaauthenticationsuppressnull-username aaaauthenticationloginsslvpnlocal aaaauthorizationnetworksslvpnlocal ! noipdomainlookup ! cryptopkitrustpointcsr1kv.local enrollmentselfsigned subject-namecn=csr1kv.local revocation-checknone rsakeypaircsr1kv.local ! ! cryptopkicertificatechaincsr1kv.local certificateself-signed01 B84230DF77267A70ADBEF7753791C3CFEF45FF13637343C99589D487E0F4D050 3E1A1CEECEFCC9F8168F91A2D62EE440A1674943D20F8EDBDB465130109147BE 99C342C5921D3DBD910CBECB5638 quit #此处为自签名证书,具体的生成过程略。 ! usernameadminprivilege15secret5$1$bVLV$u0lFX9bJ3IFSF7M6R7UFe. usernameciscopassword7060506324F41 ! ! cryptosslproposalsslvpn-proposal protectionrsa-3des-ede-sha1rsa-rc4128-md5rsa-aes128-sha1rsa-aes256-sha1 #SSL的加密策略 ! cryptosslauthorizationpolicysslvpn-auth-policy poolsslvpn dns10.1.1.100 def-domainiteachs.com routesetaccess-listsslvpn-tunnel #SSL的授权策略 ! cryptosslpolicysslvpn-policy sslproposalsslvpn-proposal pkitrustpointcsr1kv.localsign ipaddresslocal202.100.1.100port443 ! cryptosslprofilesslvpn-profile matchpolicysslvpn-policy aaaauthenticationuser-passlistsslvpn aaaauthorizationgroupuser-passlistsslvpnsslvpn-auth-policy authenticationremoteuser-pass max-users100 ! ! cryptovpnanyconnectbootflash:/anyconnect-win-4.6.03049-webdeploy-k9.pkgsequence1 ! interfaceLoopback0 ipaddress10.1.1.1255.255.255.0 ! interfaceGigabitEthernet1 ipaddress202.100.1.100255.255.255.0 negotiationauto ! iplocalpoolsslvpn172.16.1.1172.16.1.100 iproute192.168.100.0255.255.255.0202.100.1.1 ipaccess-liststandardsslvpn-tunnel permit10.1.1.00.0.0.255 !
相关查看
csr1kv#showversion CiscoIOSXESoftware,Version03.16.06.S-ExtendedSupportRelease CiscoIOSSoftware,CSR1000VSoftware(X86_64_LINUX_IOSD-UNIVERSALK9-M),Version15.5(3)S6,RELEASESOFTWARE(fc3) TechnicalSupport:http://www.cisco.com/techsupport Copyright(c)1986-2017byCiscoSystems,Inc. CompiledMon24-Jul-1720:01bymcpre CiscoIOS-XEsoftware,Copyright(c)2005-2017byciscoSystems,Inc. Allrightsreserved.CertaincomponentsofCiscoIOS-XEsoftwareare licensedundertheGNUGeneralPublicLicense("GPL")Version2.0.The softwarecodelicensedunderGPLVersion2.0isfreesoftwarethatcomes withABSOLUTELYNOWARRANTY.Youcanredistributeand/ormodifysuch GPLcodeunderthetermsofGPLVersion2.0.Formoredetails,seethe documentationor"LicenseNotice"fileaccompanyingtheIOS-XEsoftware, ortheapplicableURLprovidedontheflyeraccompanyingtheIOS-XE software. ROM:IOS-XEROMMON csr1kvuptimeis39minutes Uptimeforthiscontrolprocessoris40minutes SystemreturnedtoROMbyreload Systemimagefileis"bootflash:packages.conf" Lastreloadreason:Unknownreason ThisproductcontainscryptographicfeaturesandissubjecttoUnited Statesandlocalcountrylawsgoverningimport,export,transferand use.DeliveryofCiscocryptographicproductsdoesnotimply third-partyauthoritytoimport,export,distributeoruseencryption. Importers,exporters,distributorsandusersareresponsiblefor compliancewithU.S.andlocalcountrylaws.Byusingthisproductyou agreetocomplywithapplicablelawsandregulations.Ifyouareunable tocomplywithU.S.andlocallaws,returnthisproductimmediately. AsummaryofU.S.lawsgoverningCiscocryptographicproductsmaybefoundat: http://www.cisco.com/wwl/export/crypto/tool/stqrg.html Ifyourequirefurtherassistancepleasecontactusbysendingemailto export@cisco.com. LicenseLevel:ax LicenseType:Default.Novalidlicensefound. NextreloadlicenseLevel:ax ciscoCSR1000V(VXE)processor(revisionVXE)with1090313K/6147Kbytesofmemory. ProcessorboardID9ZMT9E7R1HJ 4GigabitEthernetinterfaces 32768Kbytesofnon-volatileconfigurationmemory. 3022272Kbytesofphysicalmemory. 7774207Kbytesofvirtualharddiskatbootflash:. Configurationregisteris0x2102 csr1kv#
csr1kv#showcryptosslsession SSLprofilename:sslvpn-profile Client_Login_NameClient_IP_AddressNo_of_ConnectionsCreatedLast_Used cisco192.168.100.100100490029 csr1kv#showcryptosslsessionusercisco Interface:SSLVPN-VIF0 SessionType:FullTunnel ClientUser-Agent:AnyConnectWindows4.6.03049 Username:ciscoNumConnection:1 PublicIP:192.168.100.100 Profile:sslvpn-profile Policy:sslvpn-policy Last-Used:0036Created:*0852.328UTCThuDec62018 TunnelIP:172.16.1.1Netmask:0.0.0.0 RxIPPackets:2TxIPPackets:28 csr1kv# csr1kv# csr1kv#
csr1kv#showcryptosslsessionuserciscodetail Interface:SSLVPN-VIF0 SessionType:FullTunnel ClientUser-Agent:AnyConnectWindows4.6.03049 Username:ciscoNumConnection:1 PublicIP:192.168.100.100 Profile:sslvpn-profile Policy:sslvpn-policy Last-Used:0000Created:*0852.328UTCThuDec62018 SessionTimeout:43200IdleTimeout:1800 DNSprimary:10.1.1.100WINSprimary:None DNSsecondary:NoneWINSsecondary:None IP6DNSprimary:None IP6DNSsecondary:None DPDGWTimeout:300DPDCLTimeout:300 AddressPool:sslvpn MTUSize:1406 DisconnectTime:0 RekeyTime:3600 LeaseDuration:43200Keepalive:30 TunnelIP:172.16.1.1Netmask:0.0.0.0 RxIPPackets:2TxIPPackets:34 CSTPStarted:0032Last-Received:0000 CSTPDPD-Reqsent:0 Msie-ProxyServer:None Msie-PxyOption:Disabled Msie-Exception:None SplitDNS:None ACL:sslvpn-tunnel DefaultDomain:iteachs.com ClientPorts:49190 DetailSessionStatisticsforUser::cisco ---------------------------------- CSTPStatistics:: RxCSTPFrames:36TxCSTPFrames:0 RxCSTPBytes:2537TxCSTPBytes:120 RxCSTPDataFr:34TxCSTPDataFr:2 RxCSTPCNTLFr:2TxCSTPCNTLFr:0 RxCSTPDPDReq:0TxCSTPDPDReq:0 RxCSTPDPDRes:0TxCSTPDPDRes:0 RxAddrRenewReq:0TxAddressRenew:0 RxDroppedFrames:0TxDroppedFrame:0 RxIPPackets:2TxIPPackets:34 RxIPBytes:120TxIPBytes:2249 RxIP6Packets:0TxIP6Packets:0 RxIP6Bytes:0TxIP6Bytes:0 CEFStatistics:: RxCSTPDataFr:0TxCSTPDataFr:0 RxCSTPBytes:0TxCSTPBytes:0 csr1kv# csr1kv#
实验完。
审核编辑:刘清
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
路由器
+关注
关注
22文章
3732浏览量
113849 -
DNS
+关注
关注
0文章
218浏览量
19856 -
iOS
+关注
关注
8文章
3395浏览量
150668 -
SSL
+关注
关注
0文章
125浏览量
25744
原文标题:Cisco IOS-XE如何配置SSL连接?
文章出处:【微信号:网络技术干货圈,微信公众号:网络技术干货圈】欢迎添加关注!文章转载请注明出处。
发布评论请先 登录
相关推荐
如何使用AT CIPSTART命令进行SSL连接?
我想从我的ESP8266到实现 SSL 套接字的服务器建立 SSL 连接。当然,我必须使用以下 AT 命令:
在 cipsslsize
在 cipstart
....但是,我如何(以及在哪里)可以上传证书、密钥等?
发表于 07-16 08:16
InRouter与Cisco Router构建L2tp VPN的方法
2.2 网络拓扑说明 中心端设备为Cisco Router 2821,IOS 为C2800NM-ADVIPSERVICESK9-M,版本15.0(1)M8;外部IP地址173.17.99.100,掩码
发表于 07-26 08:25
[分享]Cisco交换机IOS升级故障排除
Cisco交换机IOS升级故障排除交换机运行中出现故障是不可避免的,但出现故障后应当迅速地进行处理,尽快查出故障点,排除故障。但是要做到这一点,就必须了解交换机故障的类型及具备对故障进行分析和处理
发表于 06-02 11:42
Cisco Unity Express语音邮件
Express的另一个主要优势在于:它能够简化网络管理,尤其是在通常缺乏现场技术专家的中小型机构中。随时轻松添加全新话音业务的灵活性使该解决方案 更具优势。 Cisco Unity Express还提供配置
发表于 11-13 21:50
Cisco 650-180 最新资讯
three reside on the UC500 platform? (Choose three)A. Cisco IOSB.
Cisco Unity ExpressC. Cisco
发表于 06-07 13:24
Cisco 650-180 最新资讯
three reside on the UC500 platform? (Choose three)A. Cisco IOSB.
Cisco Unity ExpressC. Cisco I
发表于 06-08 09:28
如何使用AT+CIPSTART命令进行SSL连接?
我想建立从我的 ESP8266 到实现 SSL 套接字的服务器的 SSL 连接。所以,当然,我需要以下 AT 命令:
- AT+CIPSTART
- AT+CIPSSLSIZE
但是....我不知道如何(以及在哪里)上传证
发表于 05-19 09:09
CISCO路由器配置实例
Cisco 路由器的基本配置百余例目录1.用户通过DDN专线接入ISP 2.远程用户拨号连入局域网 3.远程用户间对拨 4.Cisco HSRP的
发表于 08-31 09:46
•46次下载
CISCO_2511终端服务器简单配置
cisco 终端访问服务器配置
配置终端访问服务器
试验环境,不可缺少的应用
大家在做实验是经常面临这样的一个问题,就是在操作多台设备时
发表于 10-22 16:47
•33次下载
如何配置Cisco PIX防火墙
如何配置Cisco PIX防火墙
在配置PIX防火墙之前,先来介绍一下防火墙的物理特性。防火墙通常具有至少3个接口,但许多早期的防火墙只具有
发表于 01-13 13:26
•586次阅读
CISCO路由器初始配置手册
CISCO路由器初始配置手册
很多初学路由器知识的网友对路由器的初始配置可能感到很陌生,本人在初学时也很困惑,因为一下出来很多提
发表于 04-01 11:49
•838次阅读
ssl是什么意思
ssl是什么意思,SSL安全套接层及其继任者传输层安全TLS是为网络通信提供安全及数据完整性的一种安全协议。TLS与SSL在传输层对网络连接进行加密
发表于 12-21 16:01
•1.5w次阅读
cisco交换机几种配置模式之间如何切换?
cisco交换机几种配置模式之间如何切换? 首先,我们需要了解几种常见的Cisco交换机配置模式和它们各自的作用。 1. 用户模式(User Exec Mode) 用户模式是交换机的默




 Cisco IOS-XE如何配置SSL连接?
Cisco IOS-XE如何配置SSL连接?










评论