介绍
Konan是一个开源的用于Web目录扫描的工具,针对目录和文件名。类似的还有DirBuster,dirmap等。下面也对其它类似工具的功能对比。
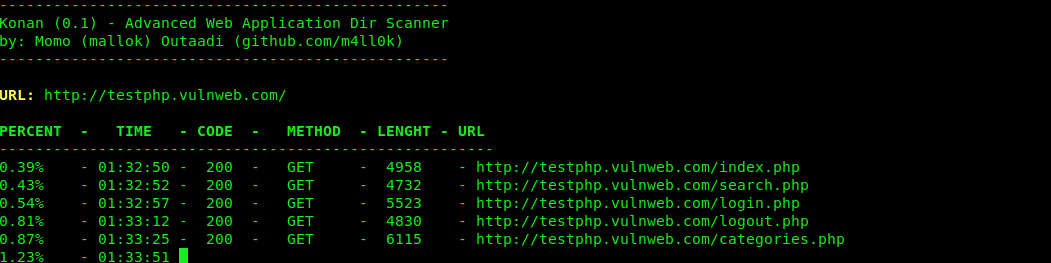
Konan目录扫描
支持平台
Windows
MacOSX
同类工具功能对比
| 功能 | Konan | dirsearch | dirb | gobuster |
|---|---|---|---|---|
| 多线程 | yes | yes | yes | yes |
| 支持多扩展 | yes | yes | no | no |
| HTTP代理支持 | yes | yes | yes | yes |
| 报告 | yes (text and json) | yes (text and json) | yes (text) | no |
| 随机代理 | yes | yes | no | no |
| 正则 regexp忽略单词 | yes | no | no | no |
| 字典拆分扩展名 | yes | no | no | no |
| 多种方法 | yes | no | no | no |
| 响应大小过程 | yes | no | no | no |
| 暴力破解子目录 | yes | no | no | no |
| 暴力破解递归子目录 | yes | no | no | no |
| URL注入点 | yes | no | no | no |
Konan安装
git clone https://github.com/m4ll0k/Konan.git konan cd konan && pip install -r requirements.txt
运行
python konan.py
Konan使用
基本:
python konan.py -u/--url http://example.com/
URL: http://testphp.vulnweb.com/ PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.39% - 01:32:50 - 200 - GET - 4958 - http://testphp.vulnweb.com/index.php 0.43% - 01:32:52 - 200 - GET - 4732 - http://testphp.vulnweb.com/search.php 0.54% - 01:32:57 - 200 - GET - 5523 - http://testphp.vulnweb.com/login.php 0.81% - 01:33:12 - 200 - GET - 4830 - http://testphp.vulnweb.com/logout.php 8.77% - 01:40:02 - 302 - GET - 14 - http://testphp.vulnweb.com/userinfo.php -> login.php
注入点:
python konan.py -u/--url http://example.com/%%/index.php
URL: http://testphp.vulnweb.com/%%/index.php PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.39% - 01:32:50 - 200 - GET - 4958 - http://testphp.vulnweb.com/test/index.php 0.43% - 01:32:52 - 200 - GET - 4732 - http://testphp.vulnweb.com/search/index.php
python konan.py -u/--url http://example.com/test%% -w /root/numbers.txt
URL: http://testphp.vulnweb.com/test%% PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.39% - 0150 - 200 - GET - 4958 - http://testphp.vulnweb.com/test12 0.43% - 0152 - 200 - GET - 4732 - http://testphp.vulnweb.com/test34
字典扫描, 默认 /db/dict.txt:
python konan.py -u/--url http://example.com/ -w/--wordlist /root/dict.txt
Provide extensions with-e/--extensionoption and force extension for every wordlist entry with-f/--forceoption:
python konan.py -u/--url http://example.com/ -e/--extension php,html -f/--force
URL: http://testphp.vulnweb.com/ PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.39% - 0221 - 200 - GET - 4958 - http://testphp.vulnweb.com/index.html 0.43% - 0223 - 200 - GET - 4732 - http://testphp.vulnweb.com/search.php 0.54% - 0230 - 200 - GET - 5523 - http://testphp.vulnweb.com/login.php 0.81% - 0246 - 200 - GET - 4830 - http://testphp.vulnweb.com/logout.html 0.87% - 0250 - 200 - GET - 6115 - http://testphp.vulnweb.com/categories.html状态码排除:
python konan.py -u/--url http://example.com/ -x/--exclude 400,403,401
仅提供输出的状态代码:
python konan.py -u/--url http://example.com/ -o/--only 200,301,302
字典小写 (isATest -> isatest) 和大写 (isAtest -> ISATEST):
python konan.py -u/--url http://example.com/ -w/--wordlist /root/dict.txt [-l/--lowercase OR -p/--uppercase]
字典拆分 (test.php -> to -> test): python konan.py -u/--url http://example.com/ -w/--wordlist /root/dict.txt -s/--split Wordlist Ignore word,letters,number,..etc provided by regexp (w*.php|w*.html,^[0-9_-]+):_
python konan.py -u/--url http://example.com/ -w/--wordlist -I/--ignore "?+"
Output without-I/--ignoreoptions:
URL: http://testphp.vulnweb.com/ PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.39% - 0231 - 200 - GET - 4958 - http://testphp.vulnweb.com/???.php 0.43% - 0232 - 200 - GET - 4732 - http://testphp.vulnweb.com/??????????? 0.54% - 0235 - 200 - GET - 5523 - http://testphp.vulnweb.com/admin/Output with-I/--ignore(in this case?+) options:
URL: http://testphp.vulnweb.com/ PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.54% - 02:06:35 - 200 - GET - 5523 - http://testphp.vulnweb.com/admin/
递归:
python konan.py -u/--url http://example.com/ -E/--recursive
Recursive directory found and directory provided by-D/--dir-rec:
python konan.py -u/--url http://example.com/ -E/--recursive -D/--dir-rec "admin,tests,dev,internal"
暴力破解目录-S/--sub-dir:
python konan.py -u/--url http://example.com/ -S/--sub-dir "admin,test,internal,dev"
多种方法 (检查 GET,POST,PUT 和 DELETE 输入词):
Note: Much web application if not make the request with right method return 404 code, this option test all methods
python konan.py -u/--url http://example.com/ -m/--methods"
Content size process (show response if the response size is ">[number]","<[number]","=[number]"):
python konan.py -u/--url http://example.com/ -C/--length "<1000"
URL: http://testphp.vulnweb.com/ PERCENT - TIME - CODE - METHOD - LENGTH - URL ------------------------------------------------------- 0.19% - 02:11:46 - 301 - GET - 184 - http://testphp.vulnweb.com/admin -> http://testphp.vulnweb.com/admin/ 1.73% - 02:12:37 - 301 - GET - 184 - http://testphp.vulnweb.com/images -> http://testphp.vulnweb.com/images/
责任编辑:彭菁
-
Web
+关注
关注
2文章
1263浏览量
69458 -
开源
+关注
关注
3文章
3344浏览量
42491
原文标题:一款高级Web目录扫描爆破工具
文章出处:【微信号:菜鸟学安全,微信公众号:菜鸟学安全】欢迎添加关注!文章转载请注明出处。
发布评论请先 登录
相关推荐
labview web 发布工具
专业python web编程工具
labview web发布工具问题
一款web综合扫描工具
多线程的web目录扫描工具
Acunetix Web Vulnerability Scanner(AWVS)工具简介
OAScan:用来扫描oa的漏洞工具
常见的漏洞扫描工具




 Konan:用于Web目录扫描的工具
Konan:用于Web目录扫描的工具











评论