非匿名密钥证明(ArkTS)
在使用本功能前,需申请权限:ohos.permission.ATTEST_KEY。请开发者根据应用的APL等级,参考具体的操作路径[权限申请]。
开发步骤
- 确定密钥别名keyAlias,密钥别名最大长度为64字节。
- 初始化参数集。
[HuksOptions]中的properties字段中的参数必须包含[HUKS_TAG_ATTESTATION_ID_SEC_LEVEL_INFO],[HUKS_TAG_ATTESTATION_CHALLENGE]属性,可选参数包含[HUKS_TAG_ATTESTATION_ID_VERSION_INFO],[HUKS_TAG_ATTESTATION_ID_ALIAS]属性。 - 生成非对称密钥,具体请参考[密钥生成]。
- 将密钥别名与参数集作为参数传入[huks.attestKeyItem]方法中,即可证明密钥。
`HarmonyOS与OpenHarmony鸿蒙文档籽料:mau123789是v直接拿`
/*
* 以下以attestKey的Promise接口操作验证为例
*/
import { huks } from '@kit.UniversalKeystoreKit';
/* 1.确定密钥别名 */
let keyAliasString = "key attest";
let aliasString = keyAliasString;
let aliasUint8 = StringToUint8Array(keyAliasString);
let securityLevel = StringToUint8Array('sec_level');
let challenge = StringToUint8Array('challenge_data');
let versionInfo = StringToUint8Array('version_info');
let attestCertChain: Array< string >;
class throwObject {
isThrow: boolean = false;
}
/* 封装生成时的密钥参数集 */
let genKeyProperties: Array< huks.HuksParam > = [
{
tag: huks.HuksTag.HUKS_TAG_ALGORITHM,
value: huks.HuksKeyAlg.HUKS_ALG_RSA
},
{
tag: huks.HuksTag.HUKS_TAG_KEY_SIZE,
value: huks.HuksKeySize.HUKS_RSA_KEY_SIZE_2048
},
{
tag: huks.HuksTag.HUKS_TAG_PURPOSE,
value: huks.HuksKeyPurpose.HUKS_KEY_PURPOSE_VERIFY
},
{
tag: huks.HuksTag.HUKS_TAG_DIGEST,
value: huks.HuksKeyDigest.HUKS_DIGEST_SHA256
},
{
tag: huks.HuksTag.HUKS_TAG_PADDING,
value: huks.HuksKeyPadding.HUKS_PADDING_PSS
},
{
tag: huks.HuksTag.HUKS_TAG_KEY_GENERATE_TYPE,
value: huks.HuksKeyGenerateType.HUKS_KEY_GENERATE_TYPE_DEFAULT
},
{
tag: huks.HuksTag.HUKS_TAG_BLOCK_MODE,
value: huks.HuksCipherMode.HUKS_MODE_ECB
}
]
let genOptions: huks.HuksOptions = {
properties: genKeyProperties
};
/* 2.封装证明密钥的参数集 */
let attestKeyproperties: Array< huks.HuksParam > = [
{
tag: huks.HuksTag.HUKS_TAG_ATTESTATION_ID_SEC_LEVEL_INFO,
value: securityLevel
},
{
tag: huks.HuksTag.HUKS_TAG_ATTESTATION_CHALLENGE,
value: challenge
},
{
tag: huks.HuksTag.HUKS_TAG_ATTESTATION_ID_VERSION_INFO,
value: versionInfo
},
{
tag: huks.HuksTag.HUKS_TAG_ATTESTATION_ID_ALIAS,
value: aliasUint8
}
]
let huksOptions: huks.HuksOptions = {
properties: attestKeyproperties
};
function StringToUint8Array(str: string) {
let arr: number[] = [];
for (let i = 0, j = str.length; i < j; ++i) {
arr.push(str.charCodeAt(i));
}
return new Uint8Array(arr);
}
function generateKeyItem(keyAlias: string, huksOptions: huks.HuksOptions, throwObject: throwObject) {
return new Promise< void >((resolve, reject) = > {
try {
huks.generateKeyItem(keyAlias, huksOptions, (error, data) = > {
if (error) {
reject(error);
} else {
resolve(data);
}
});
} catch (error) {
throwObject.isThrow = true;
throw (error as Error);
}
});
}
/* 3.生成密钥 */
async function publicGenKeyFunc(keyAlias: string, huksOptions: huks.HuksOptions) {
console.info(`enter promise generateKeyItem`);
let throwObject: throwObject = { isThrow: false };
try {
await generateKeyItem(keyAlias, huksOptions, throwObject)
.then((data) = > {
console.info(`promise: generateKeyItem success, data = ${JSON.stringify(data)}`);
})
.catch((error: Error) = > {
if (throwObject.isThrow) {
throw (error as Error);
} else {
console.error(`promise: generateKeyItem failed, ${JSON.stringify(error)}`);
}
});
} catch (error) {
console.error(`promise: generateKeyItem input arg invalid, ${JSON.stringify(error)}`);
}
}
/* 4.证明密钥 */
function attestKeyItem(keyAlias: string, huksOptions: huks.HuksOptions, throwObject: throwObject) {
return new Promise< huks.HuksReturnResult >((resolve, reject) = > {
try {
huks.attestKeyItem(keyAlias, huksOptions, (error, data) = > {
if (error) {
reject(error);
} else {
resolve(data);
}
});
} catch (error) {
throwObject.isThrow = true;
throw (error as Error);
}
});
}
async function publicAttestKey(keyAlias: string, huksOptions: huks.HuksOptions) {
console.info(`enter promise attestKeyItem`);
let throwObject: throwObject = { isThrow: false };
try {
await attestKeyItem(keyAlias, huksOptions, throwObject)
.then((data) = > {
console.info(`promise: attestKeyItem success, data = ${JSON.stringify(data)}`);
if (data !== null && data.certChains !== null) {
attestCertChain = data.certChains as string[];
}
})
.catch((error: Error) = > {
if (throwObject.isThrow) {
throw (error as Error);
} else {
console.error(`promise: attestKeyItem failed, ${JSON.stringify(error)}`);
}
});
} catch (error) {
console.error(`promise: attestKeyItem input arg invalid, ${JSON.stringify(error)}`);
}
}
async function AttestKeyTest() {
await publicGenKeyFunc(aliasString, genOptions);
await publicAttestKey(aliasString, huksOptions);
console.info('attest certChain data: ' + attestCertChain)
}
审核编辑 黄宇
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
鸿蒙
+关注
关注
57文章
2392浏览量
42992
发布评论请先 登录
相关推荐
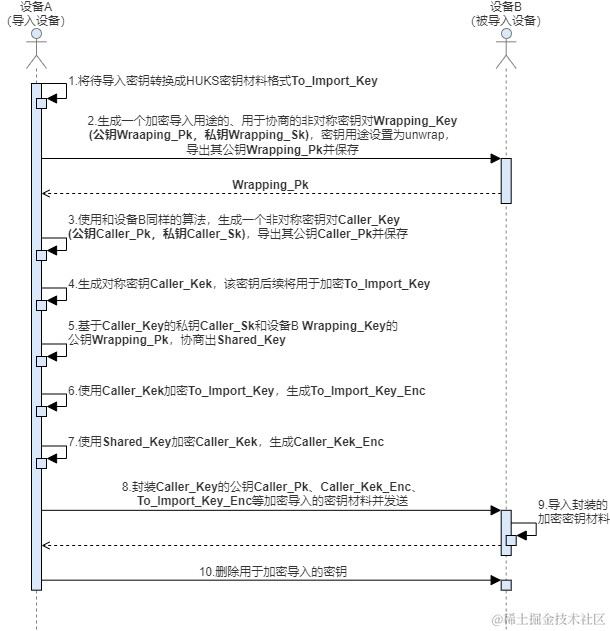
鸿蒙开发:Universal Keystore Kit密钥管理服务 密钥导入介绍及算法规格
如果业务在HUKS外部生成密钥(比如应用间协商生成、服务器端生成),业务可以将密钥导入到HUKS中由HUKS进行管理。密钥一旦导入到HUKS
鸿蒙开发:Universal Keystore Kit 密钥管理服务 密钥协商 C、C++
以协商密钥类型为ECDH,并密钥仅在HUKS内使用为例,完成密钥协商。具体的场景介绍及支持的算法规格,请参考[密钥生成支持的算法]。

鸿蒙开发:Universal Keystore Kit 密钥管理服务 HMAC ArkTS
HMAC是密钥相关的哈希运算消息认证码(Hash-based Message Authentication Code),是一种基于Hash函数和密钥进行消息认证的方法。
鸿蒙开发:Universal Keystore Kit密钥管理服务 密钥证明介绍及算法规格
HUKS为密钥提供合法性证明能力,主要应用于非对称密钥的公钥的证明。
鸿蒙开发:Universal Keystore Kit 密钥管理服务 获取密钥属性ArkTS
HUKS提供了接口供业务获取指定密钥的相关属性。在获取指定密钥属性前,需要确保已在HUKS中生成或导入持久化存储的密钥。
鸿蒙开发:Universal Keystore Kit 密钥管理服务 获取密钥属性C C++
HUKS提供了接口供业务获取指定密钥的相关属性。在获取指定密钥属性前,需要确保已在HUKS中生成或导入持久化存储的密钥。




 鸿蒙开发:Universal Keystore Kit 密钥管理服务 非匿名密钥证明ArkTS
鸿蒙开发:Universal Keystore Kit 密钥管理服务 非匿名密钥证明ArkTS












评论